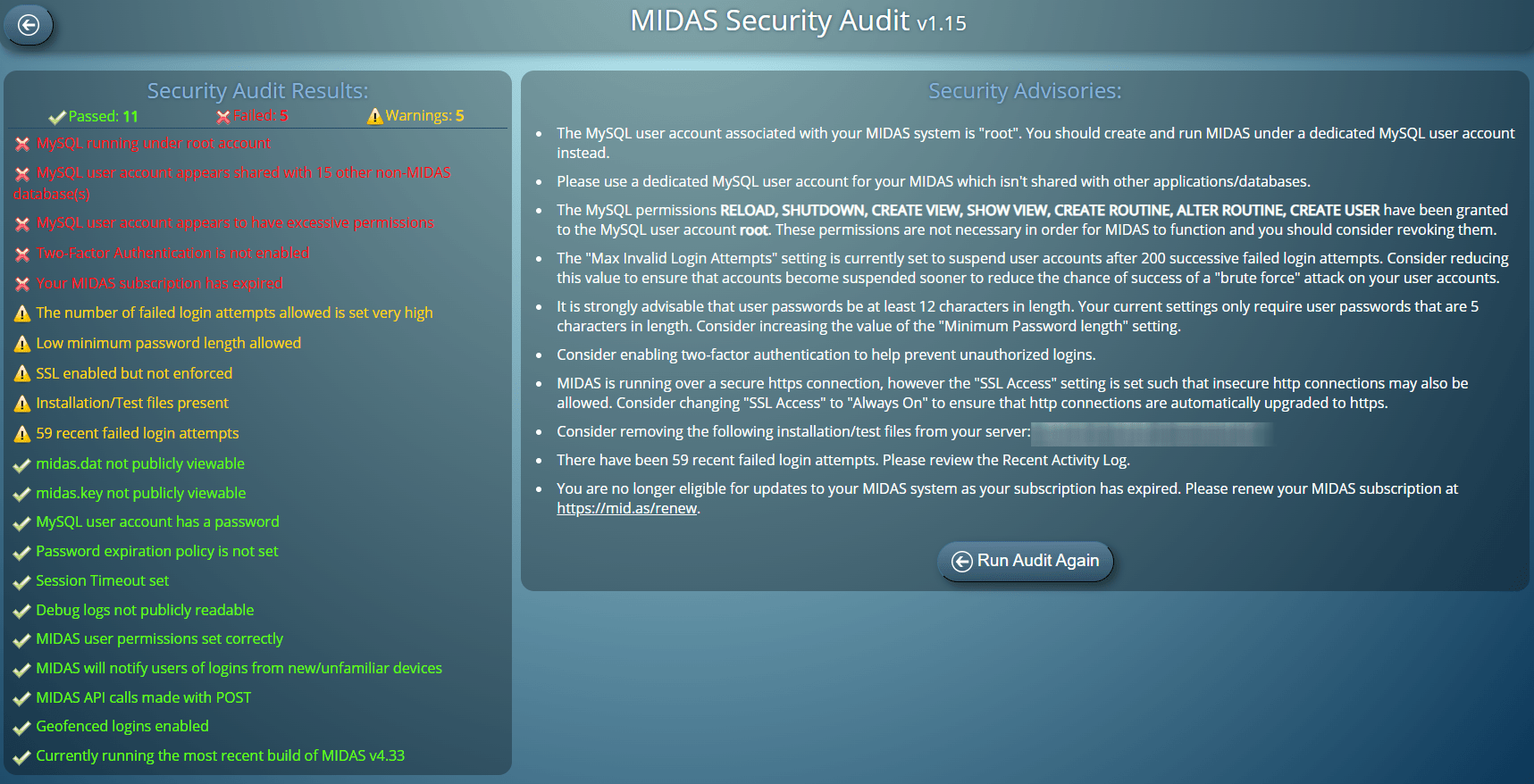
Transport Layer Security – or “TLS”- is a cryptographic mechanism to facilitate secure connections and communications across the internet. For example, the https network connection between your device and secure websites or applications, like MIDAS.
Several incarnations of the Transport Layer Security protocol have been developed over the years, the most recent being 1.3:
| Protocol | Released | Current Status |
|---|---|---|
| TLS 1.0 | 1999 | Deprecated |
| TLS 1.1 | 2006 | Deprecated |
| TLS 1.2 | 2008 | In use since 2008 |
| TLS 1.3 | 2018 | In use since 2018 |
TLS 1.0 and 1.1 are now considered “legacy protocols” and “weak” by today’s cryptographic standards. That’s because they’re susceptible to several vulnerabilities. Modern web browsers automatically default to preferring more secure TLS 1.2 and 1.3 connections. In fact, they may even display a warning when connecting to a website that only supports the now obsolete TLS 1.0/1.1 protocols.
As security and cryptographic standards have evolved over the years, we have too! We’ve previously dropped support for TLS 1.0 connections to our network in 2017. We then subsequently dropped support for TLS 1.1 connections in 2020.
As part of our ongoing commitment to security, we’re now proposing to also deprecate support for TLS 1.2 connections to our client servers in early 2025. Going forward, we propose to only support TLS 1.3 (the latest Transport Layer Security protocol version) connections.
But wait.. isn’t TLS 1.2 still considered secure?
In the past few years, researchers have discovered cryptographic weakness in some of the ciphers and algorithms that TLS 1.2 uses.
While TLS 1.2 can still be used, it is no longer considered the most secure option. TLS 1.2 is only considered “safe” when weak ciphers and algorithms are removed.
On the other hand, TLS 1.3 supports the latest modern encryption with stronger encryption algorithms and more robust authentication mechanisms. TLS 1.3 is currently the most secure TLS version. At time of writing, TLS 1.3 currently has no known vulnerabilities, and also offers performance improvements over TLS 1.2.
When will TLS 1.2 be deprecated?
At time of writing, there has been no date announced as to when TLS 1.2 will be officially deprecated.
However, one day TLS 1.2 will become obsolete, just as its predecessors TLS 1.1 and TLS 1.0 have become.
TLS 1.3 is currently the most secure TLS version. We’re keen to aid its adoption and to ensure the most secure connections to our network and servers. This is why we’re proposing to stop supporting older TLS 1.2 connections in 2025.
What impact would disabling TLS 1.2 support have?
Most modern browsers and operating systems support TLS 1.3.
Therefore, the vast majority of users will be unaffected by our proposal to switch off support for TLS 1.2 in early 2025. However, if you’re using an older device or operating system, you may need to take action.
Here’s a list of browsers and devices that will be affected when TLS 1.2 connections are blocked:
- Internet Explorer: No versions of Internet Explorer do not support TLS 1.3. This should not impact any of our users, as our MIDAS software has not been supported in IE since 2019.
- Edge Legacy: Versions of Edge Legacy prior to April 2018 do not support TLS 1.3. Users would need to update to a newer version of Edge or a different browser.
- Safari on macOS 10.12 Sierra or earlier: These older macOS versions do not support TLS 1.3 in Safari. Users would need to upgrade their macOS or use a different browser.
- Very old versions of other browsers: Browsers that haven’t been updated in several years might not support TLS 1.3.
- Older Android devices: Devices running Android 9 (and earlier versions) do not support TLS 1.3.
- Older iOS devices: Devices running iOS 12 (and earlier versions) do not support TLS 1.3.
Web browsers and devices that do support TLS 1.3:
- Microsoft Edge (current versions): Supported since April 2018 (Edge 79+)
- Google Chrome: Supported since April 2018 (Chrome 70+)
- Mozilla Firefox: Supported since October 2017 (Firefox 63+)
- Apple Safari (on macOS 10.13 High Sierra or later): Supported since September 2018 (Safari 14+)
- Opera: Supported since April 2018 (Opera 57+)
- Android: Android 10 (or later)
- iOS: iOS 13 (or later)
Important Information For Hosted API users:
If you’re a cloud-hosted MIDAS customer utilizing the optional MIDAS API you may need to take action before TLS 1.2 connections to our network are disabled in 2025.
You’ll need to ensure that your applications and the underlying programming language you develop in can support (and are correctly configured for) TLS 1.2 connections.
For instance Java 7 (1.7) (and lower) and .NET 4.7 (and lower) languages don’t support TLS 1.1/1.2.
If your applications/programming languages do not support TLS 1.3 encryption, your MIDAS API calls will begin to fail in early 2025 once we disable TLS 1.2 support across our network.
Please refer to the vendor of your programming language if you’re unsure whether it supports TLS 1.3, or for assistance enabling such support in your development environment.
Remind me again.. when is this all happening?
Currently, we are proposing to drop support for TLS 1.2 connections to our network in 2025.
We have not fixed a specific date in 2025 for this as yet (as we want to hear from you – see below).
However, anything can change over the course of a year. Should new vulnerabilities be discovered in TLS 1.2 during 2024, this may prompt us to bring our plans to deprecate 1.2 support forward.
We Want To Hear From You!
We are currently only proposing to deprecate TLS 1.2 connections to our network in 2025.
However, we’re open to feedback from you our users in the meantime.
If you feel you have a particular usage case that would require continued reliance on TLS 1.2 support, please reach out to us to discuss.