Have you ever hit the reload/refresh button in your browser whilst logged into MIDAS? Were you surprised to be bounced back to a login screen when you did? Well no more!
We’ve redesigned and improved the sign-in experience for MIDAS v4.39.
In previous versions, two options were offered on the sign-in screen..
Remember Me

Previously, the login screen included a “Remember Me” tick box. If this was selected when a user logged in, MIDAS would store their credentials in a cookie. The next time they accessed the login screen in the same browser, MIDAS would read this cookie and automatically populate the various fields on the login screen.
Auto-Login
An optional “Auto-Login” box was also present on the login screen whenever the “Remember Me” box was selected.
If “Auto-Login” was also selected, then the next time the user accessed the login screen, MIDAS would not only read the ‘remember me’ cookie and automatically populate the fields on the login screen, but also automatically click the “Login” button.
Drawbacks
There were a number of drawbacks to this approach. The primary drawback being that the “Remember Me” option stored a user’s credentials in a cookie. Whilst this data was encoded and obfuscated, it is no longer best practice to store such data in this manner.
The “Remember Me” option is also now somewhat outdated redundant. It was first introduced some 16 years ago – way back with MIDAS v2 in September 2009. Back then, password managers weren’t really a thing, and web browsers themselves didn’t provide a means to remember logins to websites.
Nowadays, all modern browsers off users the ability to remember credentials to websites and webapps. In addition, third party password managers are now also common place.
So it was time to give the “Remember Me” function a complete overhall.
In doing so, we also wanted to address a frustration which a number of our customers have reported over the years. If, when using MIDAS, they accidentally hit their browser’s reload/refresh button, MIDAS jumps them back to a login screen. (That is, unless they had selected both the “Remember Me” and the “Auto-Login” options when they initially logged in).
To combat this frustration, and to simplify the number of options on the MIDAS login screen, starting with v4.39 users will see a single “Stay signed in” option on their sign in screen.
The previous “Remember Me” and “Auto-login” options have been removed.
Staying signed in
Selecting this new “Stay signed in” option when signing in will keep the user signed-in to MIDAS on that browser until they sign out (or until their session times out, based upon the security settings setup by an administrator in your booking system.
Here’s how the new sign-in screen looks:
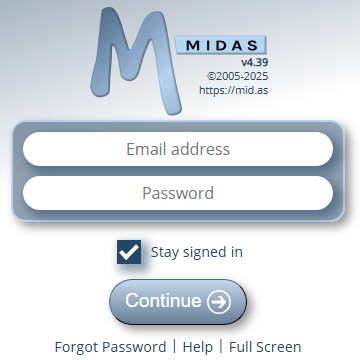
Like the previous “Remember Me” option, the new “Stay signed in” option also stores data in a cookie. However, unlike the former, the new “Stay Signed In” option only stores a randomly generated and unique session ID. No credentials themselves are stored in a cookie.
Refreshing and Reloading
Regardless of whether the new “Stay signed in” option is selected on a user’s sign-in screen, once the user has signed in, hitting refresh or reload in their browser will no longer jump the user back to a login screen – they will remain signed in!
With the “Stay signed in” option selected (and assuming the user isn’t accessing via a private/incognito browser window), the user can completely close their browser, and the next time they open it and access your MIDAS URL, they will still be signed in.
Security Considerations
Naturally, if the browser/device you use is shared by multiple people, then you should not select the “Stay signed in” option when signing in to MIDAS.
An administrative setting also exists to prevent the “Stay signed in” option from being shown to users.
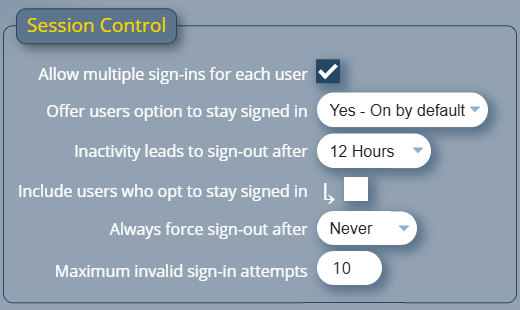
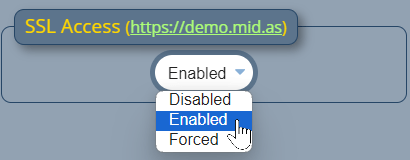
An administrator may also still wish to force user’s sessions to expire if there is an extended period of no activity. To accommodate this, new settings have been added to the Session Control section of the security screen. This screen may be accessed via MIDAS Admin Options → Manage MIDAS → Security.