As part of our ongoing commitment to security, you may notice that “Security Enhancements” often appears in the changelog when we release new builds.
In this blog post we’ll shed some light on some of the “security enhancements” that were recently introduced in MIDAS v4.11 and v4.12.
IP Change Detection
Starting with MIDAS v4.12, If a logged in user’s IP address changes whilst they are logged in, then the system will automatically log the user account out, forcing the user to log in again.
It’s rare that a user’s IP address would legitimately change mid-session, so this additional security enhancement will not be noticed by the majority of our users.
What it does do however is strengthen user sessions against a “session hijack“. In general terms, a “session hijack” is when a malicious attacker takes over a user account by gaining access to the unique identifying token (or cookie) of an active user session.
With the new IP Change Detection implemented in MIDAS v4.12, should a user fall victim to a session hijack, the session would be immediately invalidated as the originating IP address would suddenly change from the valid user’s IP address, to the IP address of the attacker.
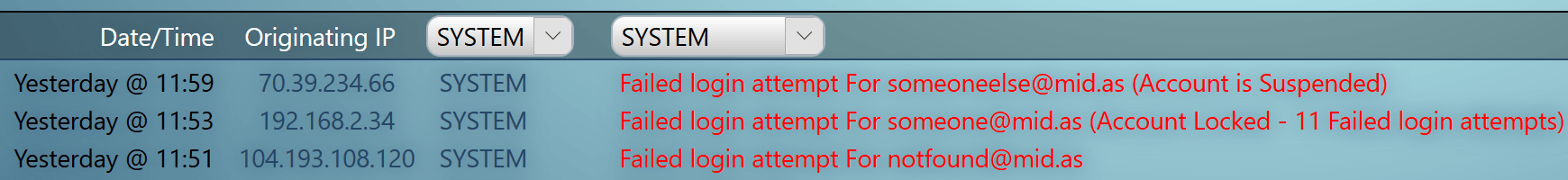
→ Tip: User’s IP addresses are also logged in each MIDAS system’s Recent Activity Log
Shorter Cookie Persistence
We’ve all come across website with “Remember Me” or “Keep Me Logged In” tick boxes on login screens. These mean that you don’t have to remember your username & password for the site each time you come to log in. When you select this box, information is stored in a browser “cookie” and retrieved the next time you visit.
MIDAS has included a “Remember Me” tickbox on the login screen since v4.07 (September 2014). Previously, the cookie saved by your browser would persist until 1st January 2020 – some 4 years in the future!
This meant that if you were to log in to MIDAS today, you could come back to the same browser in a few years time, and still log in without needing to remember your credentials.
We felt this was a little too long for your browser to be retaining such data. Therefore, from MIDAS v4.12 the “Remember Me” option will only remember your details for a period of 90 days. If you don’t log in again within this period, you’ll have to manually enter your email address/password again the next time you do.
Why is this better? Well, it ensures that “dormant” user accounts (those not logged into for over 90 days) don’t have lingering login details persisting in client-side cookies.
→ Tip: MIDAS Administrators can choose to disable the “Remember Me” option completely. This may be done via MIDAS Admin Options → Manage MIDAS → Security
Improved Session Control
In MIDAS v4.11, we introduced a new security setting to automatically log out any users that have remained logged-in for more than a set number of hours. This setting may be found under MIDAS Admin Options → Manage MIDAS → Security → Session Control.
This is different to existing “inactivity” logout setting, which causes users to be logged off after a period of no activity. The additional “Always force logout after…” setting automatically logs users off after a set period of time, regardless if they are “active” or not.
Why is this useful? Well, browser extensions/addons exist which automatically “reload” a webpage at a recurring interval. This could potentially allow a user account to remain logged-in indefinitely, even if the “Inactivity forces logout after…” setting was set.
For example, if “Inactivity forces logout after…” setting in MIDAS was set to “1 hour”, then usually 1 hour after a user’s last interaction with MIDAS, they will be automatically logged off. However, if an addon/extension were setup to “reload” part of MIDAS every 30 minutes, this would look like “user activity” to MIDAS, and so the account would never be automatically logged out.
To combat this, the new additional “Always force logout after…” setting was introduced for v4.11. If your business usually runs 9am-5pm, you could set this setting to 8 hours. This will mean that no user account can remained logged in for more than 8 hours in total. So if a user was to log in at 9am and use a browser addon/extension to effectively remain logged in all day, they will still be automatically logged out of MIDAS at 5pm.
New Session Manager
MIDAS can be configured to allow concurrent logins to user accounts from multiple browsers/devices. When enabled, this allows a user to be concurrently logged into MIDAS from their laptop, phone, and tablet.
MIDAS v4.11 introduced a new “Session Manager“. This allows users to see other devices they’re currently logged in from. The session manager shows the IP address and browser of each session, and allows you to remotely log out!
Improved Password Change Behavior
MIDAS offers the ability to allow multiple concurrent logins to the same user account. In v4.11 we’ve enhanced this security. We’ve made it so that if a user changes their MIDAS password, all other devices they’re currently logged into from will be automatically logged out. Previously, changing a password from one device wouldn’t take effect on other devices a user was logged into until the next time they logged in.
Cryptographically-secure Random Number Generation
MIDAS stores passwords which are SHA512 hashed and randomly “salted”. The “randomness” of this “salt” has been improved starting with v4.11. Now, if the Perl module “Math::Random::Secure” is available on the server where a MIDAS system resides, MIDAS will utilize it to generate cryptographically-secure random numbers.
| You might also be interested in: Tips For Keeping Your MIDAS Secure |

 We take a very pro-active approach to the security of our customer’s MIDAS systems and data, and we always strive to provide administrators and users alike with a wealth of security features and settings within our software.
We take a very pro-active approach to the security of our customer’s MIDAS systems and data, and we always strive to provide administrators and users alike with a wealth of security features and settings within our software.
