Table of Contents
← Hide Table of Contents
 Active Directory Integration: Configuring Web Browsers
Active Directory Integration: Configuring Web Browsers
In order to use MIDAS with Active Directory integration, a modification to your users' browser security settings is required in order to confirm that it is safe to exchange their currently logged in credentials with MIDAS upon request.
The settings outlined in this section will need to be applied to PC's/workstations within your domain accordingly.
Configuring Microsoft Internet Explorer
In order for Internet Explorer to supply credentials to a site, the site (domain where your MIDAS resides) must be added to IE's "Local Intranet" sites. (Internet Options → Security → Local Intranet → Sites)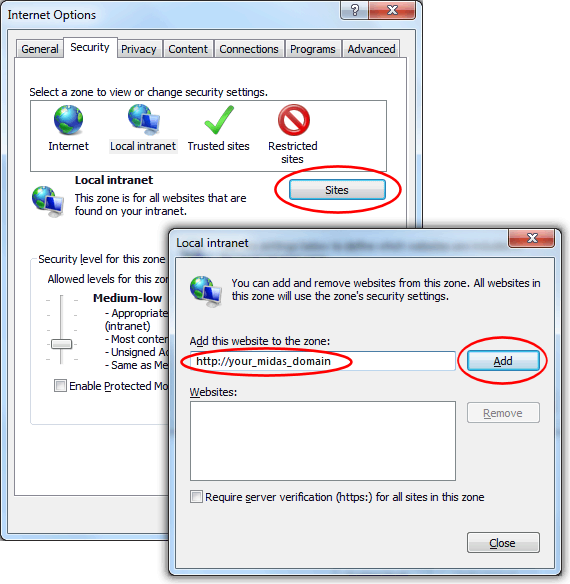
Configuring Mozilla Firefox
To configure Firefox, you will need to add the domain where your MIDAS resides as a "trusted" site for automatic authentication.To do this, open Firefox and enter "about:config" in the address bar.
Then locate the "network.automatic-ntlm-auth.trusted-uris" setting and add your MIDAS URL to this setting's current value:
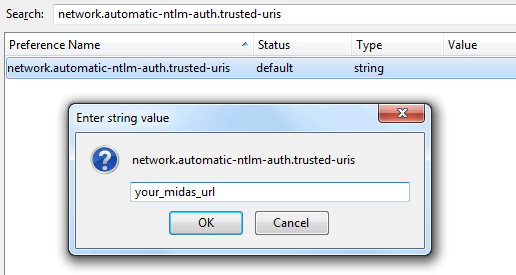
network.negotiate-auth.delegation-uris" setting as wellConfiguring Google Chrome
Chrome inherits it's from Internet Explorer's Local Intranet Zone. Therefore, please follow the steps outlined in Configuring Microsoft Internet Explorer above.Alternatively, a list of authorized servers may be passed in to Chrome using a comma-separated list of URLs via the "auth-server-whitelist" command-line switch.
For example, starting Chrome with the command-line switch:
--auth-server-whitelist="*yourdomain.com"
...will "white list" "yourdomain.com", allowing for seamless AD integration without prompting for additional credentials.
For more information, please see: https://dev.chromium.org/developers/design-documents/http-authentication
 Active Directory Integration: Configuring Web Browsers
Active Directory Integration: Configuring Web Browsers