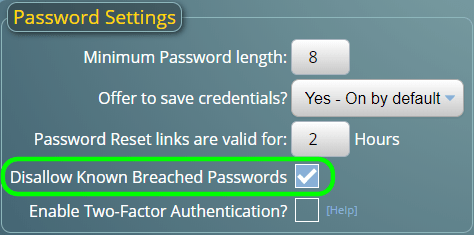
For MIDAS v4.26 we’re improving the password change process for users, with the introduction of a new “Disallow Known Breached Passwords” admin setting:
With this setting enabled, whenever a user changes their password MIDAS checks that it doesn’t appear in any known online data breaches.
Have I been Pwned?
This feature utilizes the popular 3rd party “Have I Been Pwned” service. This is a database of more than half a billion passwords which have previously been exposed in various data breaches.
Don’t worry though, your actual password is never sent to the “Have I Been Pwned” service. Here’s how it works;
- You enter a desired new password in MIDAS.
- MIDAS creates a cryptographic “hash” (SHA-1) of the password you entered. The first five characters of this hash are sent to the Have I Been Pwned service.
- If hashes with the same first five characters are found in the Pwned Passwords repository, the Have I Been Pwned service responds with all these hashes.
- MIDAS sifts through the received hashes to see if there’s a complete match with the full SHA-1 hash of your new password.
- If a match is found, your desired password has appeared in at least one public data breach. MIDAS will then display an alert and ask you to enter a different password.

The new “Disallow Known Breached Passwords” setting in MIDAS will be enabled by default. It can readily be enabled/disabled via MIDAS Admin Options → Manage MIDAS → Security.
We’re passionate about security, and this latest improvement is just one of the ways we help keep your account and MIDAS system secure.
Interested in learning more about security in your MIDAS system? Try these links…