We have a new update available to our MIDAS booking software. This update includes improvements to custom fields, booking requests, printing, privacy, and more.
Here’s what new and improved in v4.38…
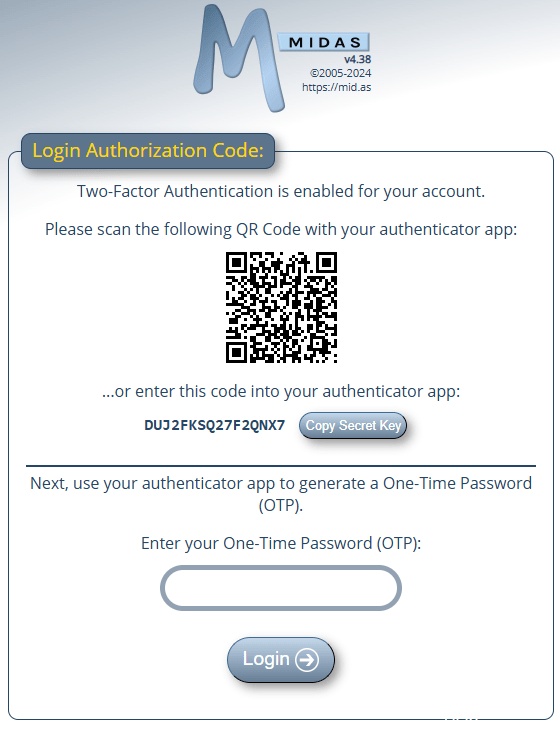
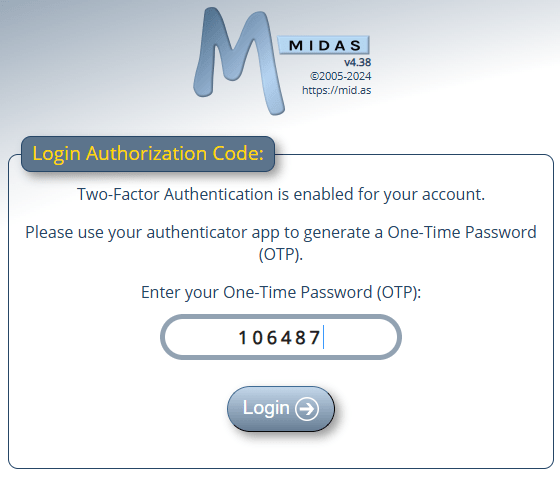
Authenticator App Support

Since 2015, all MIDAS room booking systems have included optional two-factor authentication (2FA). If enabled, this adds an additional layer of account security to our software.
With Two-Factor Authentication enabled, each time a user logins in, a code is sent to their email inbox. The user must then enter this code into MIDAS in order to complete their log in.
MIDAS v4.38 now additionally supports TOTP authenticator apps – including Google Authenticator and Microsoft Authenticator – as an alternative 2FA login option – Read more…
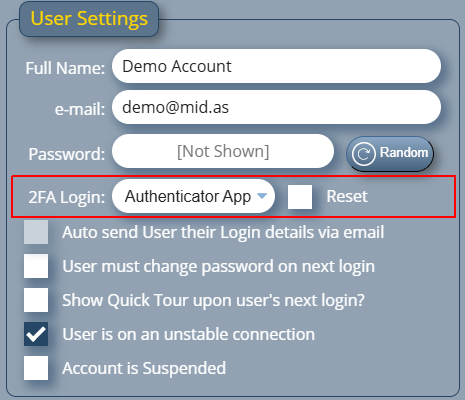
2FA Per User Account
In addition to supporting authenticator apps, we’ve also made two-factor authentication a ‘per user’ setting, rather than a ‘global’ setting.
This allows administrators to set 2FA methods for each individual user account.
Reinstall Current Version
For self-hosted customers, we’ve improved the MIDAS installer to allow re-installing your current software version without affecting your existing data/settings.
So if you accidentally delete a core file within your MIDAS installation on your web server, you can re-install MIDAS without loosing any data!
Improved Security Audit
All MIDAS systems come with a built in ‘Security Audit’ tool to assess the security of your booking system. This tool may either be run on-demand or regularly scheduled.
For MIDAS v4.38 we’ve included a new check as part of these ‘Security Audits’. This new check will alert you if there are any ‘obsolete’ user accounts within your MIDAS system. An ‘obsolete’ user account is considered to be any user account which has not been logged into for at least 6 months.
Improved Booking Grid performance
The ‘Booking Grid’ is the main area where your bookings are visually presented within MIDAS.
We’ve made some improvements to the performance of the booking grid in v4.38 by reducing the amount of data that’s initially loaded when viewing bookings for any given date.
For busy organizations with hundreds of bookings across their venues in any given day, the amount of data being loaded in the booking grid was significant, and could lead to sluggish loading.
We’ve significantly improved this for v4.38, meaning that large quantities of bookings now load and display faster than ever!
Other Improvements
This latest version of MIDAS also includes stability and performance improvements and fixes for several issues that have been detected or reported since the previous release (v4.37) – View the complete v4.38 changelog….
How To Get MIDAS v4.38…
New to MIDAS?
You can try MIDAS v4.38 for FREE with no obligation to buy!
There’s both a functional online public demo, and you can also try MIDAS free for 30 days.
We offer a choice of both cloud and self hosted solutions. So if you’re ready to get MIDAS working for your organization, purchase or subscribe today via our secure website.
“Self Hosted” Customers:
Self-Hosted customers with active Support Subscriptions can update to v4.38, and it only takes a couple of clicks.
Simply log in to your MIDAS system and go to MIDAS Admin Options → Manage MIDAS → Update.
“Cloud Hosted” Customers:
All our active Cloud-Hosted customers MIDAS systems have previously been update to v4.38.
We seamlessly apply software updates for our cloud hosted customers. So you’ll always have access to the latest features, and never need to worry about running outdated software.