SAML 2.0, or Security Assertion Markup Language 2.0, is an open standard that enables cross-domain single sign-on (SSO). It’s a process which allows one system (the “Service Provider”) to trust the authentication performed by another system (the “Identity Provider”). Essentially, it lets users authenticate once and then access multiple services without needing to re-enter their credentials every time.
Here’s how it works..
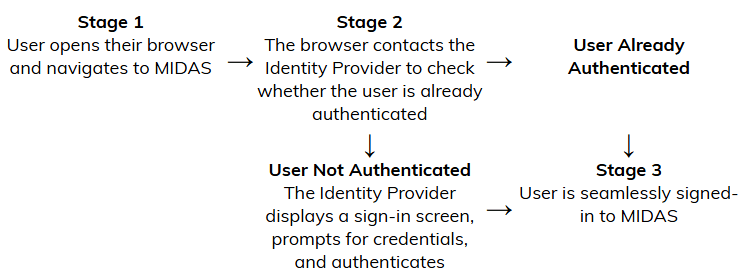
MIDAS has long supported SSO via Active Directory (LDAP) integration. From v4.40 however, our booking systems now also support seamless Single Sign-On (SSO) through SAML 2.0 Identity Providers. This allows users to be automatically logged in whenever they access MIDAS.
Unlike Active Directory integration – which was only available to those running self-hosted MIDAS booking systems, SAML 2.0 integration is available to both self-hosted and cloud-hosted systems.
What you’ll need
All you’ll need is a MIDAS system licensed for “unlimited” users. If you need to upgrade your license, you can do so at mid.as/upgrade.
You’ll then be able to configure your MIDAS system with your chosen SAML 2.0 Identity Provider.
Popular SAML 2.0 identity providers include (but are not limited to):
- Auth0
- Microsoft ADFS
- Microsoft Entra ID (formerly Azure AD)
- Okta
- OneLogin
- PingFederate
- PingOne SSO
- Shibboleth
Testing SAML 2.0 Integration
We’ve produced a handy “SAML Test Tool” that you can use to test integration between your MIDAS booking system and your chosen SAML 2.0 Identity Provider.
To use this tool, you’ll need to enter some data provided by your Identity Provider, and generate some data for your MIDAS system to encrypt and authenticate data between MIDAS and your Identity Provider. The SAML Test Tool will then verify that it can successfully communicate with your Identity Provider.
Configuration
After successfully verifying authentication with your SAML 2.0 Identity Provider using our aforementioned SAML Test Tool, you’re then ready to configure your MIDAS booking system for single sign-on.
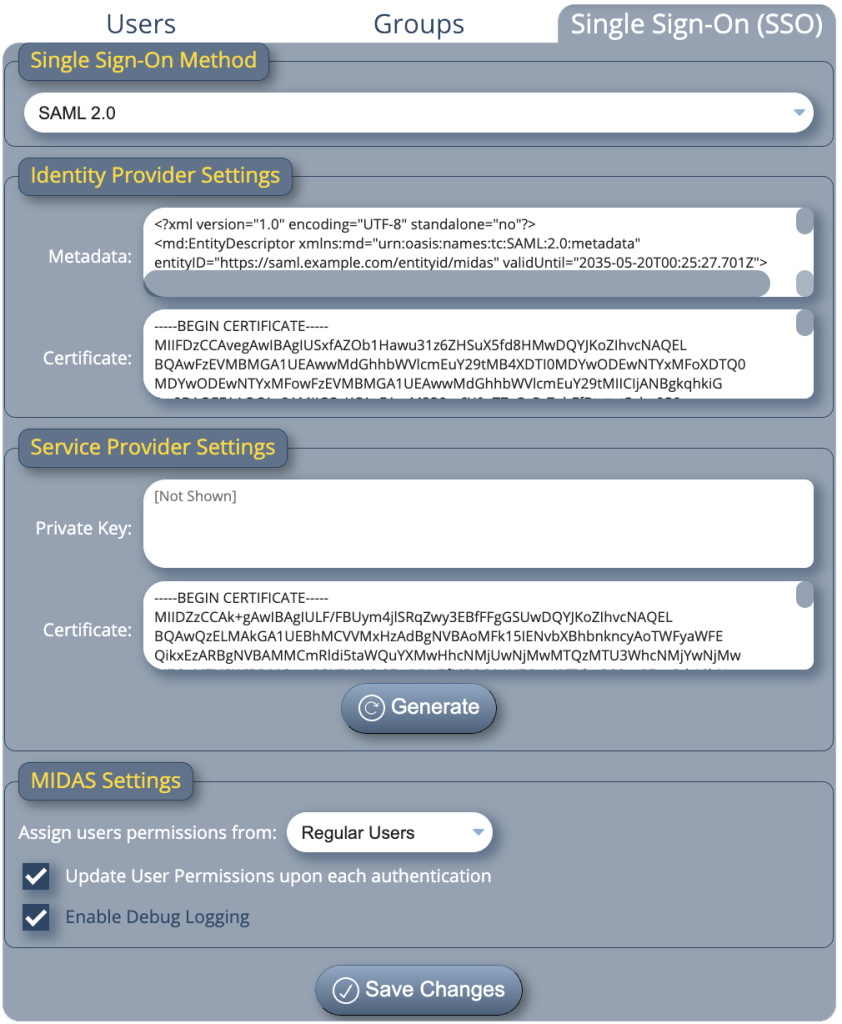
These settings may be found via MIDAS Admin Options → Manage Users & Permissions → Single Sign-On (SSO). Here you’ll be able to use modified Identity Provider settings from the SAML Test Tool, as well as Service Provider settings from the tool too. Finally, you choose which group of permissions user’s authenticating via your SAML 2.0 Identity Provider should inherit.
Find out more…
Complete documentation for SAML 2.0 integration with MIDAS is available at mid.as/saml-integration.
Please Note: SAML 2.0 integration is currently in “beta”, and so we want your feedback if you encounter any issues.