As many of you may already be aware, information was released on Tuesday this week about a major Internet vulnerability widely referred to as “Heartbleed”.
As many of you may already be aware, information was released on Tuesday this week about a major Internet vulnerability widely referred to as “Heartbleed”.
This vulnerability affected a common software library called “OpenSSL” which is a cryptography system built to encrypt passwords and other sensitive information on around two-thirds of all websites on the Internet.
Many popular websites, including Twitter, Yahoo!, Gmail and Facebook had been found vulnerable to Heartbleed, which if exploited could potentially reveal the contents of a server’s memory, including passwords and other sensitive information.
“Your popular social site, your company’s site, commerce site, hobby site, site you install software from or even sites run by your government might be using vulnerable OpenSSL“, reveals the website devoted to explaining the bug.
Whilst many of these websites have now this week been updated/patched against Heartbleed, the vulnerability itself has been present in the latest versions of OpenSSL for the past two years, but has only recently come to light and details publicly disclosed this week.
Our MIDAS servers run OpenSSL, however, we have no reason to believe that the vulnerability has been exploited to compromise the integrity or confidentiality of any of our services or of our users’ data. Even so, due to the hard-to-detect nature of the attack, we’re taking a very broad view of the potential vulnerability and have responded accordingly.
What has MIDAS done in response?
Our MIDAS servers run OpenSSL, and we’ve been proactive in making sure that our users’ data and accounts are kept safe. Specifically:
- Our servers have been patched.
As of Wednesday 9th April 03:33 UTC, all of our servers have been updated to use a newer, protected version of OpenSSL. - We’ve reset SSL keys and certificates for our public *.mid.as servers.
As of Thursday 10th April 21:51 UTC all of our public servers are using newly-generated keys and certificates. Additionally, we’ve asked AlphaSSL to revoke our old certificates, just to be on the safe side.
What can you do?
We have no reason to believe that the Heartbleed vulnerability has been exploited to compromise the integrity of any of our services or of our users’ data. Even so, if we “host” your MIDAS and you want to be extra careful, you can change your MIDAS password at any time, once logged in via the “Change Password” near the top of your MIDAS screen.
Here’s some handy tips for creating better passwords:
- Avoid using the same password for multiple websites.
- Make your passwords at least 8 characters
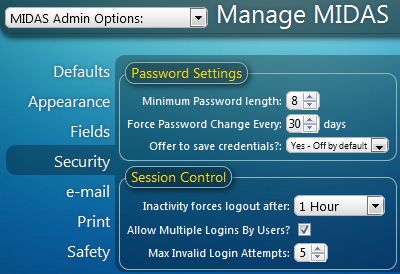
– In MIDAS, you can enforce a minimum password length for users via MIDAS Admin Options → Manage MIDAS → Security → Minimum Password Length. - Include a mixture of numbers, upper & lowercase letters, and symbols in your password
– MIDAS can randomly generate such passwords for users, via MIDAS Admin Options → Manage Users & Permissions → [select user] → Password → Random. - Avoid complete words.
- Avoid common passwords such as “123456” and “password”.